
The Cisco 350-201 certification exam verifies the storage ability of the candidate’s network security knowledge. The core content of the test is not complicated, and it is not difficult for prepared candidates.
If you have friends who have passed the exam to help you, you will get twice the result with half the effort. The second is to find more useful materials to help you practice.
I believe that even those who have obtained the Cisco Certified CyberOps Professional certification will tell you that the exam questions are updated every time. The 350-201 certification exam randomly distributes exam questions based on the total core database, so the best advice must be
It takes a lot of practice to really help you succeed.
The most effective test technique for 2023 is to practice the latest 350-201 exam questions and answers: https://www.leads4pass.com/350-201.html (139 Q&A).
Read the latest 350-201 exam questions and answers online:
| Type | Number of exam questions | Exam name | Exam code | Last updated |
| Free | 15 | Performing CyberOps Using Cisco Security Technologies (CBRCOR) | 350-201 | 350-201 dumps |
Question 1:
Refer to the exhibit. Which indicator of compromise is represented by this STIX?
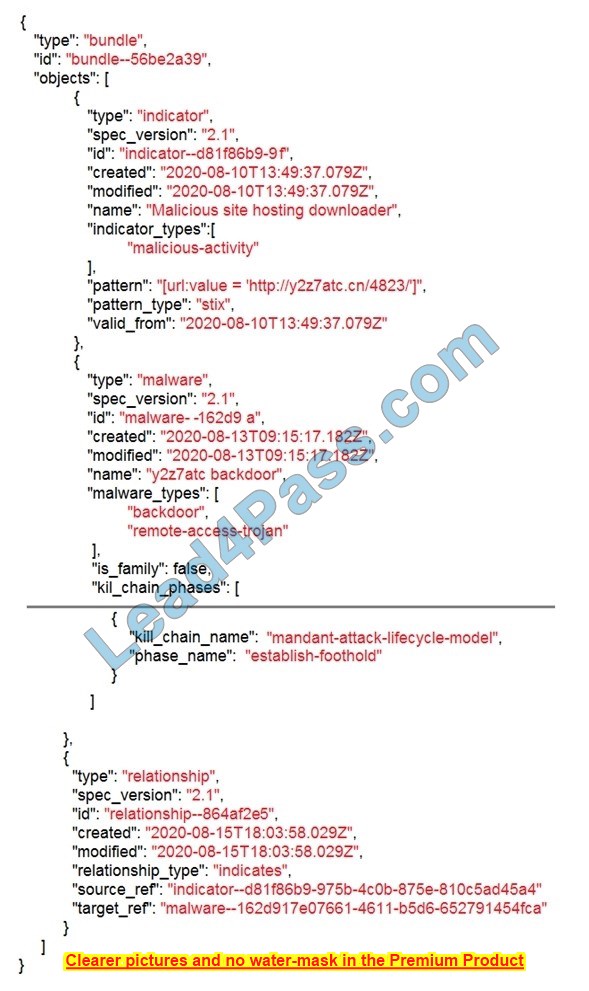
A. website redirecting traffic to ransomware server
B. website hosting malware to download files
C. web server vulnerability exploited by malware
D. cross-site scripting vulnerability to backdoor server
Correct Answer: C
Question 2:
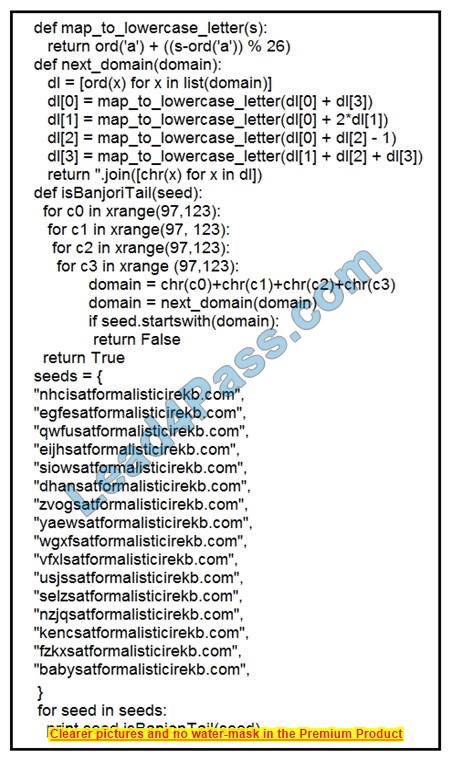
Refer to the exhibit. What results from this script?
A. Seeds for existing domains are checked
B. A search is conducted for additional seeds
C. Domains are compared to seed rules
D. A list of domains as seeds is blocked
Correct Answer: B
Question 3:
A security engineer discovers that a spreadsheet containing confidential information for nine of their employees was fraudulently posted on a competitor\’s website. The spreadsheet contains names, salaries, and social security numbers. What is the next step the engineer should take in this investigation?
A. Determine if there is internal knowledge of this incident.
B. Check incoming and outgoing communications to identify spoofed emails.
C. Disconnect the network from Internet access to stop phishing threats and regain control.
D. Engage the legal department to explore action against the competitor that posted the spreadsheet.
Correct Answer: D
Question 4:

Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
A. exploitation
B. actions on objectives
C. delivery
D. reconnaissance
Correct Answer: C
Reference: https://www2.deloitte.com/content/dam/Deloitte/sg/Documents/risk/sea-risk-cyber-101-july2017.pdf
Question 5:
Employees receive an email from an executive within the organization that summarizes a recent security breach and requests that employees verify their credentials through a provided link. Several employees report the email as suspicious, and a security analyst is investigating the reports. Which two steps should the analyst take to begin this investigation? (Choose two.)
A. Evaluate the intrusion detection system alerts to determine the threat source and attack surface.
B. Communicate with employees to determine who opened the link and isolate the affected assets.
C. Examine the firewall and HIPS configuration to identify the exploited vulnerabilities and apply recommended mitigation.
D. Review the mail server and proxy logs to identify the impact of a potential breach.
E. Check the email header to identify the sender and analyze the link in an isolated environment.
Correct Answer: CE
Question 6:
A SOC team is investigating a recent, targeted social engineering attack on multiple employees. Cross-correlated log analysis revealed that two hours before the attack, multiple assets received requests on TCP port 79. Which action should be taken by the SOC team to mitigate this attack?
A. Disable BIND forwarding from the DNS server to avoid reconnaissance.
B. Disable affected assets and isolate them for further investigation.
C. Configure affected devices to disable NETRJS protocol.
D. Configure affected devices to disable the Finger service.
Correct Answer: D
Question 7:
A threat actor used a phishing email to deliver a file with an embedded macro. The file was opened, and a remote code execution attack occurred in a company\’s infrastructure. Which steps should an engineer take at the recovery stage?
A. Determine the systems involved and deploy available patches
B. Analyze event logs and restrict network access
C. Review access lists and require users to increase password complexity
D. Identify the attack vector and update the IDS signature list
Correct Answer: B
Question 8:
DRAG DROP
Drag and drop the actions below the image onto the boxes in the image for the actions that should be taken during this playbook step. Not all options are used.
Select and Place:
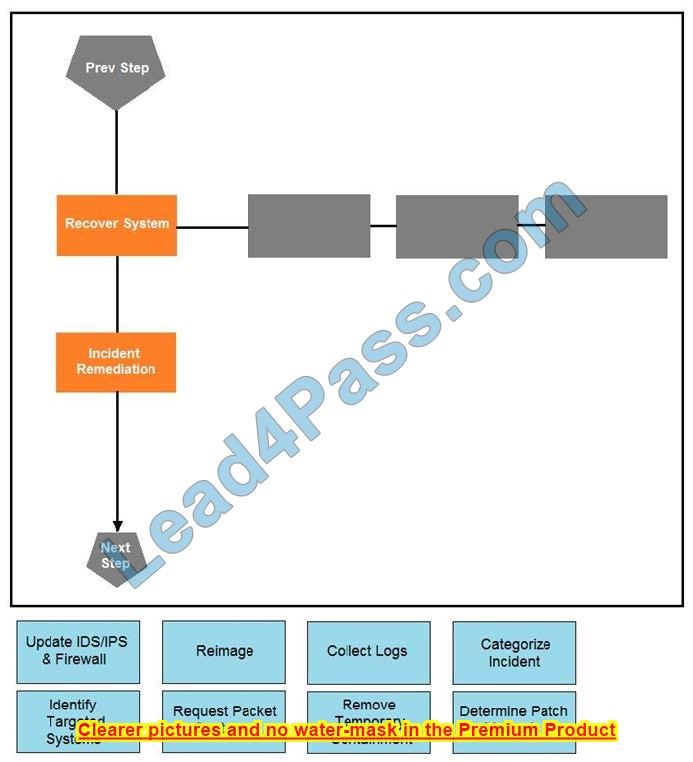
Correct Answer:
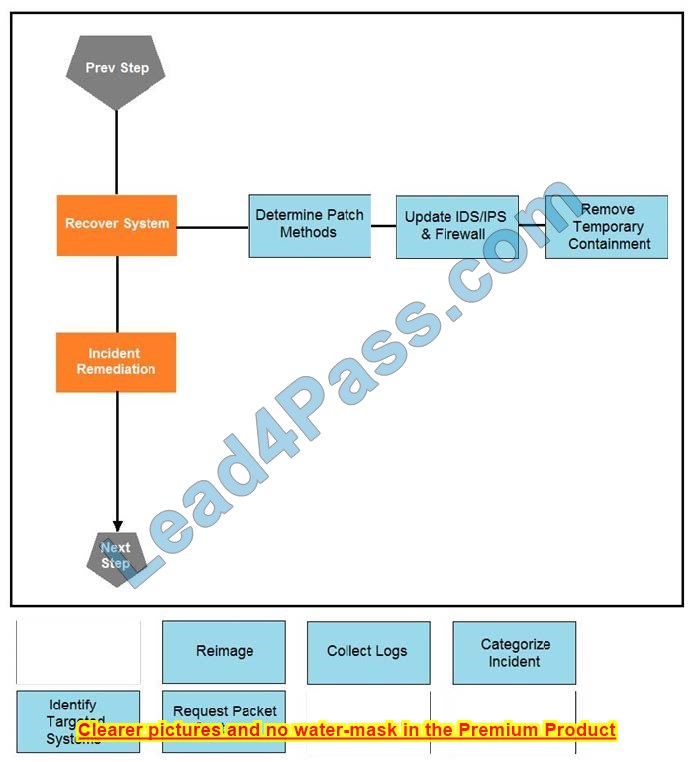
Question 9:
How does Wireshark decrypt TLS network traffic?
A. with a key log file using per-session secrets
B. using an RSA public key
C. by observing DH key exchange
D. by defining a user-specified decode-as
Correct Answer: A
Reference: https://wiki.wireshark.org/TLS
Question 10:
An engineer returned to work and realized that payments that were received over the weekend were sent to the wrong recipient. The engineer discovered that the SaaS tool that processes these payments was down over the weekend. Which step should the engineer take first?
A. Utilize the SaaS tool team to gather more information on the potential breach
B. Contact the incident response team to inform them of a potential breach
C. Organize a meeting to discuss the services that may be affected
D. Request that the purchasing department creates and sends the payments manually
Correct Answer: A
Question 11:
A new malware variant is discovered hidden in pirated software that is distributed on the Internet. Executives have asked for an organizational risk assessment. The security officer is given a list of all assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose two.)
A. incident response playbooks
B. asset vulnerability assessment
C. report of staff members with asset relations
D. key assets and executives
E. malware analysis report
Correct Answer: BE
Reference: https://cloudogre.com/risk-assessment/
Question 12:
What is the HTTP response code when the REST API information requested by the authenticated user cannot be found?
A. 401
B. 402
C. 403
D. 404
E. 405
Correct Answer: A
Question 13:
A company recently started accepting credit card payments in their local warehouses and is undergoing a PCI audit. Based on business requirements, the company needs to store sensitive authentication data for 45 days. How must data be stored for compliance?
A. post-authorization by non-issuing entities if there is a documented business justification
B. by entities that issue the payment cards or that perform support issuing services
C. post-authorization by non-issuing entities if the data is encrypted and securely stored
D. by issuers and issuer processors if there is a legitimate reason
Correct Answer: C
Question 14:
What is the impact of hardening machine images for deployment?
A. reduces the attack surface
B. increases the speed of patch deployment
C. reduces the steps needed to mitigate threats
D. increases the availability of threat alerts
Correct Answer: A
Question 15:
Refer to the exhibit. An engineer is performing static analysis of a file received and reported by a user. Which risk is indicated in this STIX?
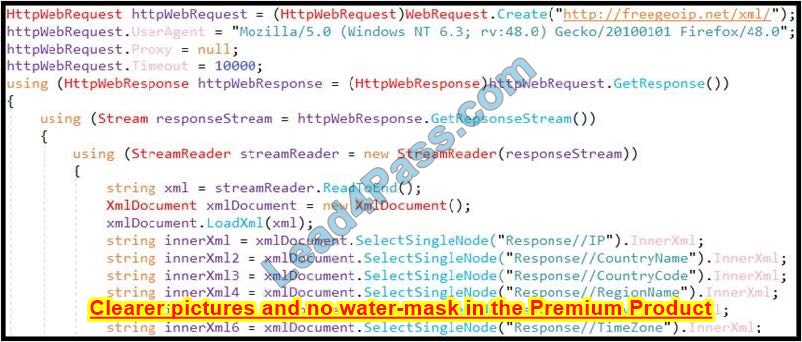
A. The file is redirecting users to a website that requests privilege escalations from the user.
B. The file is redirecting users to the website that is downloading ransomware to encrypt files.
C. The file is redirecting users to a website that harvests cookies and stored account information.
D. The file is redirecting users to a website that is determining users’ geographic location.
Correct Answer: D
…
The best 350-201 exam technique is practice, download the complete 350-201 exam practice questions: https://www.leads4pass.com/350-201.html (350-201 dumps-> 139 Q&A)
Learn more detailed 350-201 Certification Exam Tips:
Exam topics:
Understand the exam topics: The Cisco 350-201 exam covers a wide range of topics related to cyber operations and Cisco security technologies.
Make sure you have a clear understanding of the exam objectives, which can be found on the Cisco website.
Focus your study efforts on the areas where you feel less confident.
official study materials:
Use official study materials: Cisco offers a variety of study materials, such as official books, online courses, practice exams, and study groups, to help you prepare for the exam. Use these materials to supplement your study plan and gain a deeper understanding of the exam topics.
Manage your time:
Manage your time: The Cisco 350-201 exam has a time limit of 120 minutes. Use your time wisely and pace yourself during the exam.
Make sure you answer all questions and leave enough time to review your answers before submitting the exam.
…
Good luck!


