Pass the Cisco 300-175 exam test quickly and easily at first attempt with the latest Cisco 300-175 dumps exam practice questions PDF and practice exam, http://www.leads4pass.com/300-175.html download one of the many PDF readers that are available for free.
QUESTION 1
Which statement is true about the PPP Session Phase of PPPoE?
A. PPP options are negotiated and authentication is not performed. Once the link setup is completed, PPPoE functions as a Layer 3 encapsulation method that allows data to be transferred over the PPP link within PPPoE headers.
B. PPP options are not negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a Layer 4 encapsulation method that allows data to be transferred over the PPP link within PPPoE headers.
C. PPP options are automatically enabled and authorization is performed. Once the link setup is completed, PPPoE functions as a Layer 2 encapsulation method that allows data to be encrypted over the PPP link within PPPoE headers.
D. PPP options are negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a Layer 2 encapsulation method that allows data to be transferred over the PPP link within PPPoE headers.
Correct Answer: D
Explanation:
PPPoE is composed of two main phases:
Active Discovery Phase–In this phase, the PPPoE client locates a PPPoE server, called an access concentrator. During this phase, a Session ID is assigned and the PPPoE layer is established.
PPP Session Phase–In this phase, PPP options are negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a Layer 2 encapsulation method, allowing data to be transferred over the PPP link within PPPoE headers.
QUESTION 2
Refer to the exhibit.
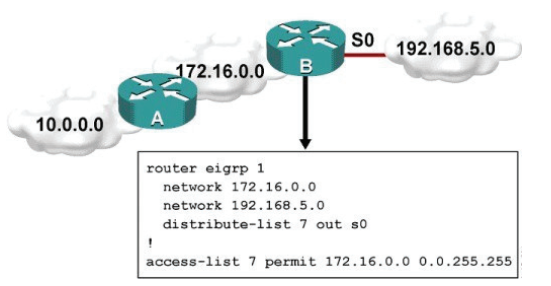
Which one statement is true? 300-175
A. Traffic from the 172.16.0.0/16 network will be blocked by the ACL.
B. The 10.0.0.0/8 network will not be advertised by Router B because the network statement for the 10.0.0.0/8 network is missing from Router B.
C. The 10.0.0.0/8 network will not be in the routing table on Router B.
D. Users on the 10.0.0.0/8 network can successfully ping users on the 192.168.5.0/24 network, but users on the 192.168.5.0/24 cannot successfully ping users on the 10.0.0.0/8 network.
E. Router B will not advertise the 10.0.0.0/8 network because it is blocked by the ACL.
Correct Answer: E
Explanation:
You can filter what individual routes are sent (out) or received (in) to any interface within your EIGRP configuration.
One example is noted above. If you filter outbound, the next neighbor(s) will not know about anything except the 172.16.0.0/16 route and therefore won’t send it to anyone else downstream. If you filter inbound, YOU won’t know about the route and therefore won’t send it to anyone else downstream.
QUESTION 3
For security purposes, an IPv6 traffic filter was configured under various interfaces on the local router. However, shortly after implementing the traffic filter, OSPFv3 neighbor adjacencies were lost. What caused this issue?
A. The traffic filter is blocking all ICMPv6 traffic.
B. The global anycast address must be added to the traffic filter to allow OSPFv3 to work properly.
C. The link-local addresses that were used by OSPFv3 were explicitly denied, which caused the neighbor relationships to fail.
D. IPv6 traffic filtering can be implemented only on SVIs.
Correct Answer: C
Explanation:
OSPFv3 uses link-local IPv6 addresses for neighbor discovery and other features, so if any IPv6 traffic filters are implemented be sure to include the link local address so that it is permitted in the filter list.
QUESTION 4
What is the purpose of the autonomous-system {autonomous-system-number} command?
A. It sets the EIGRP autonomous system number in a VRF.
B. It sets the BGP autonomous system number in a VRF.
C. It sets the global EIGRP autonomous system number.
D. It sets the global BGP autonomous system number.
Correct Answer: A
Explanation:
To configure the autonomous-system number for an Enhanced Interior Gateway Routing Protocol (EIGRP) routing process to run within a VPN routing and forwarding (VRF) instance, use the 300-175 autonomous-system command in address-family configuration mode. To remove the autonomous-system for an EIGRP routing process from within a VPN VRF instance, use the no form of this command.
QUESTION 5
Which type of traffic does DHCP snooping drop?
A. discover messages
B. DHCP messages where the source MAC and client MAC do not match
C. traffic from a trusted DHCP server to client
D. DHCP messages where the destination MAC and client MAC do not match
Correct Answer: B
Explanation:
The switch validates DHCP packets received on the untrusted interfaces of VLANs with DHCP snooping enabled. The switch forwards the DHCP packet unless any of the following conditions occur (in which case the packet is dropped):
The switch receives a packet (such as a DHCPOFFER, DHCPACK, DHCPNAK, or DHCPLEASEQUERY packet) from a DHCP server outside the network or firewall.
The switch receives a packet on an untrusted interface, and the source MAC address and the DHCP client hardware address do not match. This check is performed only if the DHCP snooping MAC address verification option is turned on. · The switch receives a DHCPRELEASE or DHCPDECLINE message from an untrusted host with an entry in the DHCP snooping binding table, and the interface information in the binding table does not match the interface on which the message was received.
The switch receives a DHCP packet that includes a relay agent IP address that is not 0.0.0.0. To support trusted edge switches that are connected to untrusted aggregation-switch ports, you can enable the DHCP option-82 on untrusted port feature, which enables untrusted aggregation- switch ports to accept DHCP packets that include option-82 information. Configure the port on the edge switch that connects to the aggregation switch as a trusted port.
QUESTION 6
A network engineer notices that transmission rates of senders of TCP traffic sharply increase and decrease simultaneously during periods of congestion. Which condition causes this?
A. global synchronization
B. tail drop
C. random early detection
D. queue management algorithm
Correct Answer: A
Explanation:
TCP global synchronization in computer networks can happen to TCP/IP flows during periods of congestion because each sender will reduce their transmission rate at the same time when packet loss occurs.
Routers on the Internet normally have packet queues, to allow them to hold packets when the network is busy, rather than discarding them.
Because routers have limited resources, the size of these queues is also limited. The simplest technique to limit queue size is known as tail drop. The queue is allowed to fill to its maximum size, and then any new packets are simply discarded, until there is space in the queue again. This causes problems when used on TCP/IP routers handling multiple TCP streams, especially when bursty traffic is present. While the 300-175 network is stable, the queue is constantly full, and there are no problems except that the full queue results in high latency. However, the introduction of a sudden burst of traffic may cause large numbers of established, steady streams to lose packets simultaneously.
Read more: http://www.leads4pass.com/300-175.html
Watch the video to learn more:
https://youtu.be/eY_9wwsP8no


